Recently, AWS announced Amazon Bedrock AgentCore, a flexible service that helps developers seamlessly create and manage AI agents across different frameworks and models, whether hosted on Amazon Bedrock or other environments. Specifically, AgentCore Runtime provides a secure, serverless, and purpose-built hosting environment for deploying and running AI agents or tools. AgentCore Runtime is framework agnostic, working seamlessly with popular frameworks like LangGraph, Strands, and CrewAI for deploying your AI agents and tools with automatic scaling and built-in security.
In this post, we demonstrate how to use a GitHub Actions workflow to automate the deployment of AI agents on AgentCore Runtime. This approach delivers a scalable solution with enterprise-level security controls, providing complete continuous integration and delivery (CI/CD) automation. By implementing a comprehensive pipeline, we enable seamless agent deployment with AWS best practices, including OpenID Connect (OIDC) authentication, least-privilege access controls, and environment separation. Our solution facilitates efficient updates for existing agents and integrates continuous security scans and rigorous code quality checks. The result is a robust deployment strategy that helps minimize operational complexity, enhance security, and accelerate AI agent development across enterprise environments.
Benefits of Amazon Bedrock AgentCore Runtime
AgentCore Runtime is the ideal service for production agent deployments:
- Provides a framework agnostic environment to run your agents
- Works with large language models (LLMs) such as models offered by Amazon Bedrock and Anthropic Claude
- Provides session isolation by running each user session in a dedicated microVM with isolated CPU, memory, and file system resources
- Supports both real-time interactions and long-running workloads up to 8 hours
- Offers built-in capabilities for authentication and observability
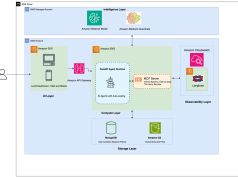
Solution overview
We’ve developed a comprehensive CI/CD pipeline with GitHub Actions that streamlines the deployment of Agents in compliance with security standard. The pipeline is available as a ready-to-use solution that can integrate seamlessly with your existing development workflow.The solution consists of the following key components:
- GitHub Actions – A workflow orchestration tool to host the pipeline
- Amazon Bedrock AgentCore Runtime – An AWS service to host and run the deployed agents
- Amazon Elastic Container Registry (Amazon ECR) – An AWS service to store, manage, and deploy container images for agents
- Amazon Inspector – An AWS service to perform advanced and continuous vulnerability scanning on container images
- IAM OIDC identity provider – A federated authentication service to establish trust between GitHub and AWS to allow GitHub Actions to deploy on AWS without maintaining AWS secrets and credentials
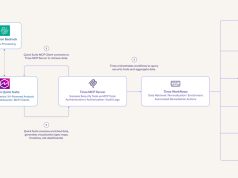
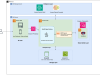
The following diagram illustrates the architecture for the solution.
The data flow consists of the following steps:
- A developer commits code changes from their local repository to the GitHub repository. In this solution, the GitHub Action is triggered manually, but this can be automated.
- The GitHub Action triggers the build stage.
- GitHub’s OIDC uses tokens to authenticate with AWS and access resources.
- GitHub Actions invokes the command to build and push the agent container image to Amazon ECR directly from the Dockerfile.
- AWS Inspector triggers an advanced security scan when the image is uploaded.
- An AgentCore Runtime instance is created using the container image.
- The agent can further query the Amazon Bedrock model and invoke tools according to its configuration.
In the following sections, we walk through the steps to deploy the solution:
- Download the source code from the GitHub repo.
- Create your agent code.
- Set up GitHub secrets.
- Create an IAM role and policies.
- Create the GitHub Actions workflow.
- Trigger and monitor the pipeline.
- Verify the deployment.
Prerequisites
Before you can use our secure CI/CD pipeline for deploying agents to AgentCore Runtime, verify you have the following prerequisites in place:
- An AWS account with sufficient permissions to create IAM Identity and Access Management (IAM) roles
- Access to the required LLM model from the supported foundation models in Amazon Bedrock
- GitHub account with Actions enabled (GitHub.com or GitHub Enterprise)
- Python 3.10+ for local development and testing
Download source code
Clone the source code repository: bedrock-agentcore-runtime-cicd
git clone https://github.com/aws-samples/sample-bedrock-agentcore-runtime-cicd.git
The repository folder consists of the following structure:
Create agent code
Create your agent with the framework of your choice using the AgentCore Runtime toolkit. The toolkit uses BedrockAgentCoreApp to create an application that provides a standardized way to package your AI agent code into a container that can run on AgentCore Runtime managed infrastructure. It also uses app.entrypoint, a Python decorator that marks a function as the main entry point. When the Amazon Bedrock agent receives the incoming API request, this function receives and processes the user’s request. In this sample agent code, when someone calls your Amazon Bedrock agent using an API, AgentCore Runtime will automatically call the strands_agent_bedrock(payload) function.
In this post, we use the agents/strands_agent.py file to create an agent using the Strands Agents framework:
Set up GitHub secrets
The GitHub Actions workflow must access resources in your AWS account. In this post, we use an IAM OpenID Connect identity provider and IAM roles with IAM policies to access AWS resources. OIDC lets your GitHub Actions workflows access resources in AWS without needing to store the AWS credentials as long-lived GitHub secrets. These credentials are stored as GitHub secrets within your GitHub repository Settings under Secrets option. For more information, see Using secrets in GitHub Actions.
Create IAM roles and policies
To run agents or tools in AgentCore Runtime, you need an IAM execution role. For information about creating an IAM role, see IAM role creation.
In this post, we create the required trust policy and execution role for AgentCore Runtime. See IAM Permissions for AgentCore Runtime for more details.
The following code is for the AgentCore Runtime trust policy:
The following code is for the AgentCore Runtime execution role:
Create the GitHub Actions workflow
Refer the CI/CD workflow file at .github/workflows/deploy-agentcore.yml for details to create the workflow.The following steps will be performed by the workflow:
- It uses the default Ubuntu Github Runner for the task provided in the pipeline.
- The workflow installs the required dependencies mentioned in the
requirement.txtfile. - It builds the Docker image and deploys it on the ECR repository.
- The image is scanned with Amazon Inspector to identify potential vulnerabilities.
- AgentCore Runtime deploys the agent as an endpoint.
- The workflow tests the agent endpoint to verify functionality.
Trigger and monitor pipeline
This pipeline can be triggered either by changing a code in the agents folder or manually using the workflow dispatch option. This might further change according to your organization’s branching strategy. Update the code in .github/workflows/deploy-agentcore.yml to change this trigger behavior.
Test agent
After the agent is deployed, we will verify its functionality by triggering the Test Agent workflow manually via workflow dispatch option.
AgentCore Runtime versioning and endpoints
Amazon Bedrock AgentCore implements automatic versioning for AgentCore Runtime and lets you manage different configurations using endpoints. Endpoints provide a way to reference specific versions of AgentCore Runtime. For more details and sample code, see AgentCore Runtime versioning and endpoints.
Clean up
To avoid incurring future charges, complete the following steps:
- Delete the ECR images from the Amazon ECR console created through the deployment using GitHub Actions.
- Delete the agent deployed in AgentCore Runtime.
Conclusion
In this post, we demonstrated a comprehensive approach to using GitHub Actions for a more secure and scalable deployment of AI agents on AgentCore Runtime. Our solution provides a robust, automated, and controlled environment for generative AI applications, addressing critical enterprise deployment challenges by automating dependency management, implementing continuous code quality checks, performing comprehensive vulnerability scanning, and facilitating consistent deployment processes. By abstracting infrastructure complexities, this pipeline helps developers focus on agent logic and functionality, while providing a framework-agnostic approach that supports seamless management of multiple AI agents at scale. As AI agents continue to transform enterprise capabilities, this solution represents a significant step towards streamlining AI agent development and operational management, offering a standardized, secure, and efficient deployment mechanism for modern generative AI applications.
As a next step, you can use Amazon Q to intelligently enhance and customize your AI agent deployment pipeline, transforming your CI/CD processes with advanced, context-aware automation.
About the authors
 Prafful Gupta is an Assoc. Delivery Consultant at AWS based in Gurugram, India. Having started his professional journey with Amazon a year ago, he specializes in DevOps and Generative AI solutions, helping customers navigate their cloud transformation journeys. Beyond work, he enjoys networking with fellow professionals and spending quality time with family. Connect on LinkedIn at: linkedin.com/in/praffulgupta11/
Prafful Gupta is an Assoc. Delivery Consultant at AWS based in Gurugram, India. Having started his professional journey with Amazon a year ago, he specializes in DevOps and Generative AI solutions, helping customers navigate their cloud transformation journeys. Beyond work, he enjoys networking with fellow professionals and spending quality time with family. Connect on LinkedIn at: linkedin.com/in/praffulgupta11/
 Anshu Bathla is a Lead Consultant – SRC at AWS, based in Gurugram, India. He works with customers across diverse verticals to help strengthen their security infrastructure and achieve their security goals. Outside of work, Anshu enjoys reading books and gardening at his home garden. Connect on LinkedIn at: linkedin.com/in/anshu-bathla/
Anshu Bathla is a Lead Consultant – SRC at AWS, based in Gurugram, India. He works with customers across diverse verticals to help strengthen their security infrastructure and achieve their security goals. Outside of work, Anshu enjoys reading books and gardening at his home garden. Connect on LinkedIn at: linkedin.com/in/anshu-bathla/