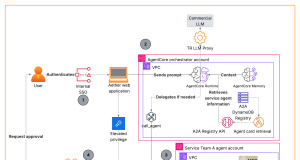
How Thomson Reuters built an Agentic Platform Engineering Hub with Amazon...
This post was co-written with Naveen Pollamreddi and Seth Krause from Thomson Reuters.
Thomson Reuters (TR) is a leading AI and technology company dedicated to...
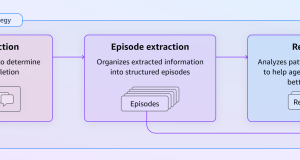
Build agents to learn from experiences using Amazon Bedrock AgentCore episodic...
Today, most agents operate only on what’s visible in the current interaction: they can access facts and knowledge, but they can’t remember how they...
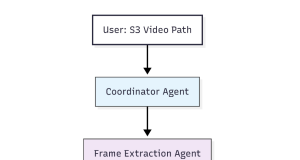
Using Strands Agents to create a multi-agent solution with Meta’s Llama...
Multi-agent solutions, in which networks of agents collaborate, coordinate, and reason together, are changing how we approach real-world challenges. Enterprises manage environments with multiple...
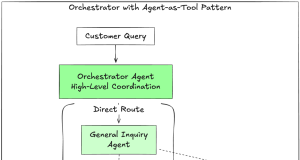
How bunq handles 97% of support with Amazon Bedrock
This post was co-authored with Benjamin Kleppe, Machine Learning Engineering Lead at bunq.
The integration of agentic AI is transforming the banking industry, marking a...
“Largest Infrastructure Buildout In Human History”: Jensen Huang on AI’s “Five-Layer...
From skilled trades to startups, AI’s rapid expansion is the beginning of the next massive computing platform shift, and for the world’s workforce a...
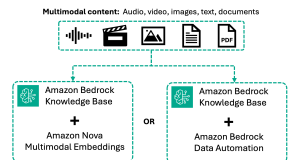
Introducing multimodal retrieval for Amazon Bedrock Knowledge Bases
We are excited to announce the general availability of multimodal retrieval for Amazon Bedrock Knowledge Bases. This new capability adds native support for video...
NVIDIA Brings GeForce RTX Gaming to More Devices With New GeForce...
Announced at the CES trade show running this week in Las Vegas, NVIDIA is bringing more devices, more games and more ways to play...
From Warehouse to Wallet: New State of AI in Retail and...
AI has transformed retail and consumer packaged goods (CPG) operations, enhancing customer analysis and segmentation to enable greater personalization for marketing and advertising, and...
More Ways to Play, More Games to Love — GeForce NOW...
NVIDIA is wrapping up a big week at the CES trade show with a set of GeForce NOW announcements that are bringing more ways...